Cryptography: The Art of Hiding

Cryptography can be defined as a method of protecting the digitally shared information between the users. In simple words, it helps us to protect our 'confidentiality' or 'privacy'.
The word cryptography consists of two words, 'crypt' which stands for 'hidden' and 'graphy' which stands for 'writing'.
Cryptography is basically related to the study of 'cryptology' and 'cryptoanalysis'. It includes various techniques such as microdot, combining words with images, merging images in audios and other different methods to maintain your confidentiality.
If we talk cryptography in terms of information security it is more often associated with scrambling or converting the plaintext into an encrypted text (or ciphertext ) and again decrypting (or decipher ) the encrypted text into the plain text. When we talk about cryptography we will always come across the two words, i.e, Encryption and Decryption. So let us talk about it.
Encryption and Decryption:
Encryption can be referred to as the method of converting plain text ( common language ) into a ciphertext ( an encrypted text which cannot be read by unauthorized access ) and decryption can be referred to as the method of converting the ciphertext back into the plain text ( i.e, decipher ). For encryption, we use a cipher, which is basically an algorithm (set of instructions) and the individual having the encryption key can only decrypt the encrypted text.
Types of Encryption:
There are basically two major types of encryption :
1) Symmetric Encryption
2) Asymmetric Encryption
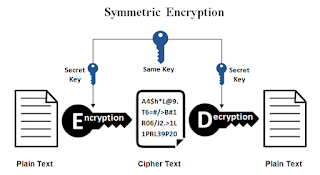 Symmetric Encryption is an encryption method that consists of only one key which can be used for both, encryption of the plain text as well as decryption of the ciphertext. It is one of the oldest methods of encryption which involves only one key (i.e, public key). Some of the popular symmetric encryption methods are blowfish, DES, AES, etc. The major disadvantage of symmetric encryption is that all the users associated with this have to share the key among them to access the data.
Symmetric Encryption is an encryption method that consists of only one key which can be used for both, encryption of the plain text as well as decryption of the ciphertext. It is one of the oldest methods of encryption which involves only one key (i.e, public key). Some of the popular symmetric encryption methods are blowfish, DES, AES, etc. The major disadvantage of symmetric encryption is that all the users associated with this have to share the key among them to access the data. Asymmetric Encryption is an encryption method that involves tho way key systems. In this type of method, the plain text is encrypted by a public key and it can only be decrypted by a private (secret key) key which is only known to the receiver. This method is a relatively new method than the symmetrical method. Some of the popular asymmetrical methods are RSA, DSA, etc. The asymmetric Encryption method is basically used in our day-to-day communication channels, especially over the internet.
Asymmetric Encryption is an encryption method that involves tho way key systems. In this type of method, the plain text is encrypted by a public key and it can only be decrypted by a private (secret key) key which is only known to the receiver. This method is a relatively new method than the symmetrical method. Some of the popular asymmetrical methods are RSA, DSA, etc. The asymmetric Encryption method is basically used in our day-to-day communication channels, especially over the internet.So there was a short introduction about cryptography, encryption and decryption, and types of encryption. If you want detailed information on Cryptography please let me know through comments.
Comments
Post a Comment